De1CTF这次队里师傅都很出力很牛逼,最后成绩也很不错,俺被直接带飞,这里对MISC做一个汇总wp,部分wp来自于队友。
mc_joinin
这题wp感谢Yoshino-s师傅(Y老师牛逼)
尝试直接用MC客户端连接IP,发现可以识别到MC服务器,但是版本号不对。然后找了一下发现了一个NodeJS的MC无头客户端minecraft-protocol。
尝试使用无头客户端自动协商版本,同时魔改使其强制切换到指定版本。(需要手动修改库文件)网页提示了原版本为1.12。
var mc = require('minecraft-protocol');
var client = mc.createClient({
host: "222.85.25.41", // optional
port: 25565,
username: "2233",
});DEBUG="minecraft-protocol" node joinin.js 2> record.txtdump出数据
{
"header": "{\n \"text\":\"\\n\\nHIDE FLAG ONE\\n\\n imgur.com/a/ZOrErVM \\n\\n\",\n \"color\":\"black\",\n \"bold\":true\n }",
"footer": "{\"translate\":\"\"}"
}访问url:imgur.com/a/ZOrErVM,下载图片,发现在最低位隐写了flag图片且经过了镜像;拉伸,处理之后读取到flag

mc_champion
这题wp也感谢Yoshino-s师傅
本来以为需要在完整版客户端里打龙,想了好久最终决定直接整个代理处理版本信息。主要部分如下
localsocket.on('data', function (data) {
console.log("%s:%d - writing data to remote",
localsocket.remoteAddress,
localsocket.remotePort
);
const hex = data.toString('hex');
console.log(hex);
if (hex === '1500cf020e3137322e32392e3139382e32303163dd02') {
console.log('Handshake');
data = Buffer.from('1000e507093132372e302e302e3163dd02', 'hex');
}
if (hex === '0b0009796f7368696e6f5f73') {
console.log('Handshake');
data = Buffer.from('06000432323333', 'hex');
}
var flushed = remotesocket.write(data);
if (!flushed) {
console.log(" remote not flushed; pausing local");
localsocket.pause();
}
});然而进去了却发现,动不了也啥东西都没有,然后经过探索又发现,就是通过输入命令打龙。
所以直接使用无头客户端脚本自动打,注意因为服务器连接不稳定,动不动TCP包解析错误直接断掉,所以需要多尝试几次。
var mc = require('minecraft-protocol');
var client = mc.createClient({
host: "222.85.25.41", // optional
port: 25565,
username: "2233",
});
/*
/help -> show the usage
/uuid -> show your uuid
/status -> show your status
/items -> show your items
/exchange -> make some exchange
/shop -> list all category
/shop [category_id] -> list items in category
/buy [item_id] -> buy the item
/use [item_id] -> use your item
/attack -> attack the BOSS
*/
let reso = null;
client.on('chat', function (packet) {
// Listen for chat messages and echo them back.
var jsonMsg = JSON.parse(packet.message);
const t = jsonMsg.text + jsonMsg.extra.map(i => i.text).join('');
console.log('Recv <- ' + t);
if (reso) {
reso(t);
}
});
async function say(s) {
console.log('Send -> ' + s);
client.write('chat', { message: s });
const ret = await Promise.race([new Promise(res => reso = res), delay(2000)]);
return ret;
}
async function delay(t) {
return new Promise(res => {
setTimeout(res, t);
});
}
const del = 1000;
setTimeout(async () => {
await say('/exchange 1');
await delay(del);
await say('/exchange 1');
await delay(del);
await say('/exchange 1');
await delay(del);
await say('/exchange 1');
await delay(del);// 初始40XP换钱
await say('/buy 5');// 买钻石剑
await delay(del);
while (1) {
await say('/attack');//攻击
await delay(del);
await say('/buy 19');
await delay(del);
await say('/use 19');
await delay(del);
await say('/buy 19');
await delay(del);
await say('/use 19');// 买两个面包,吃两个面包
await delay(del);
await say('/exchange 1');
await delay(del);
await say('/exchange 1');// 每次攻击获得20XP,换钱
await delay(del);
}
}, 2000);打完之后出来
Congratulation!
Encoded Message:
F5GUGMRQ
GIYC2RCF
IJKUOLKW
JFCVOORN
FEFFC4RR
KBDVG62G
GNYGQZJT
L5EGMTSU
GNPTA4ZN
KRBF6RTZ
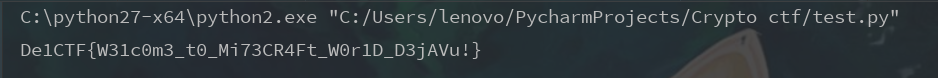
OZYHE7T5base32,然后凯撒,获得flag
Misc杂烩/Misc Chowder
题目描述和hint:
- 流量包中的网络连接对解题没有帮助 The network connection in pcap is not helping to the challenge
- 不需要访问流量里任何一个的服务器地址,所有数据都可以从流量包里直接提取 Do not need to connect the network, every data can be extracted from the pcap
- In the burst test point of compressed packet password, the length of the password is 6, and the first two characters are "D" and "E". 压缩包密码暴破考点中,密码的长度为6位,前两位为DE。
链接:https://pan.baidu.com/s/13eIrCZAoEpLXGQ8V2aJlfQ
提取码:cyym
拿到这个题目,首先看一遍流量,然后发现一个upload_file.php
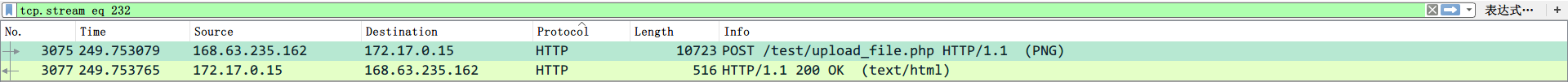
里面是传了一张png图片,保存下来,可得:
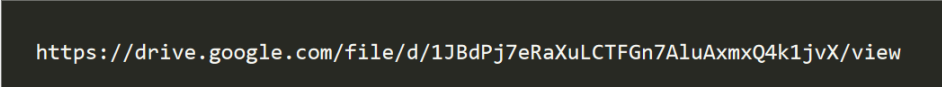
然后获得一个readme.zip文件
链接:https://pan.baidu.com/s/19xUSOq-UKa-CqO-6vXAIVA
提取码:mjih
readme.zip文件解压获得一个docx文件,里面放着两张图片。然后对docx文件binwalk -e提取出一个压缩包You_found_me_Orz.zip:
然后根据hint3进行掩码爆破,得到password为DE34Q1
解压获得一张图片,再次binwalk -e获得一个rar文件,解压发现有个flag.txt,但是提交发现不对,不是最后的flag。
那么在cmd执行dir /r,发现有隐藏的信息: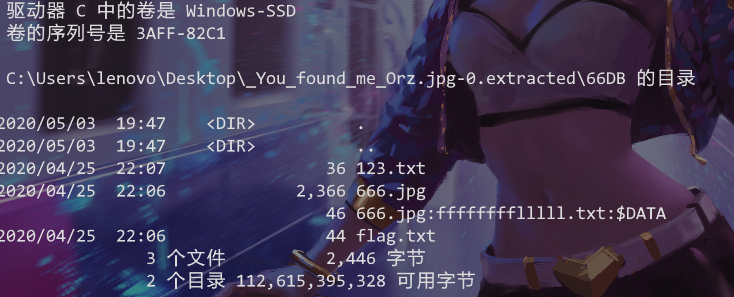
那么考虑NTFS隐写,用NtfsStreamsEditor2搜索可得最后flag:
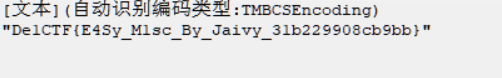
Easy Protocol
这题wp感谢ub1sof6师傅
拿到文件winhex打开是个压缩包改下后缀名发现三个流量包
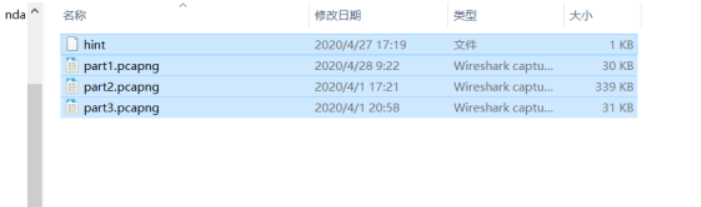
在part1中找到关键字De1CTF然后在LDAP协议中找到密钥
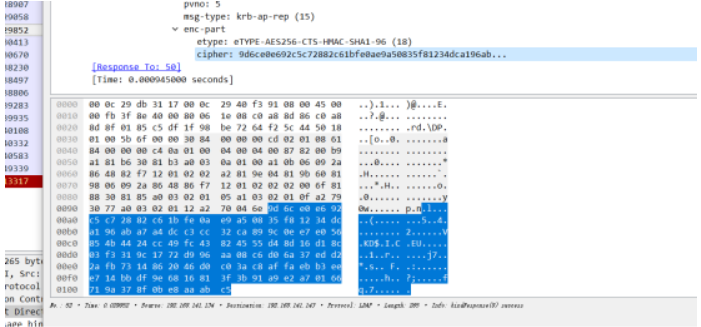
在part2中相同的方法找到密钥
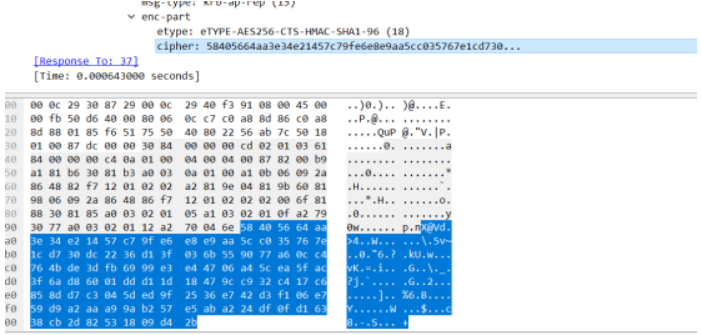
Part3有些特殊,找到了几个分
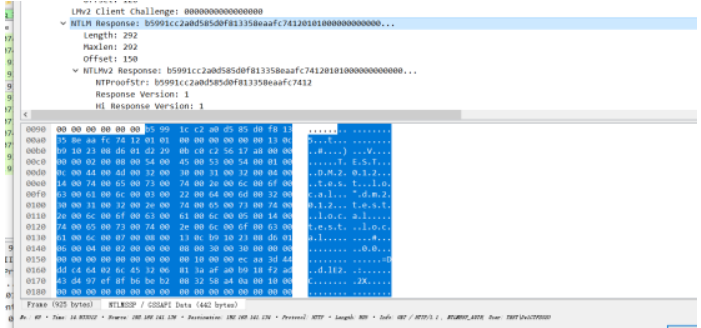
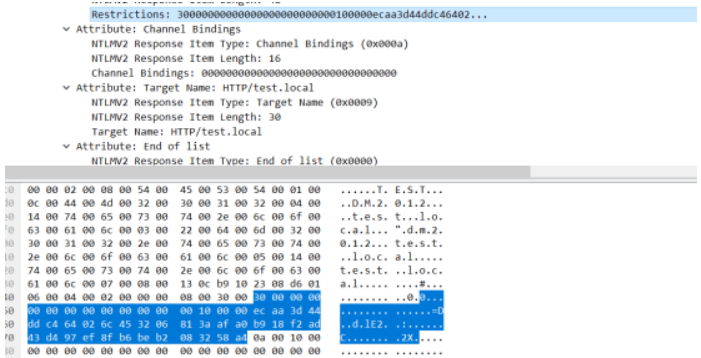
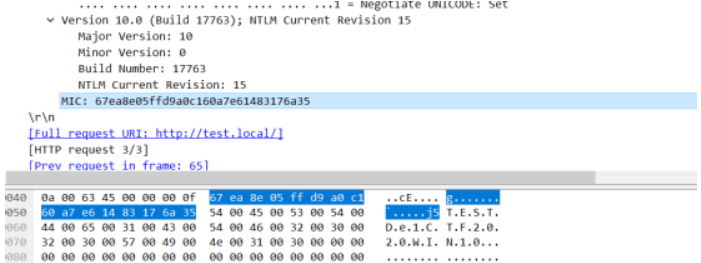
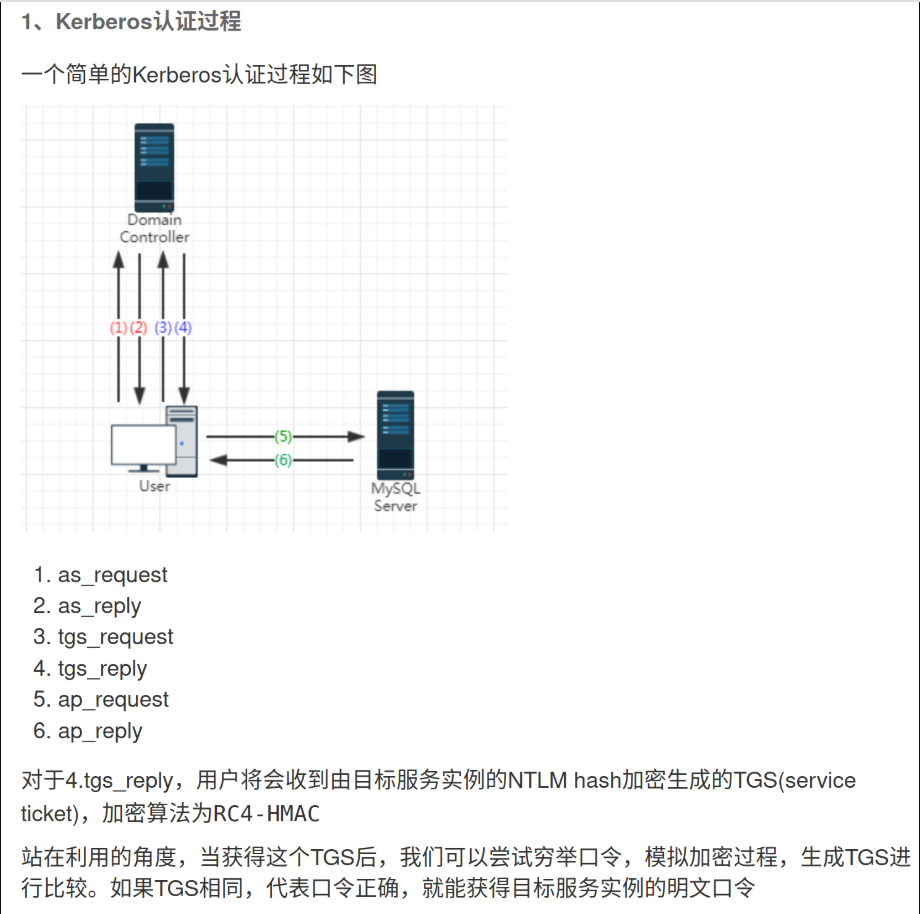
接下来使用hashcat破解Kerberos 5, etype 18, Pre-Auth 需要使用最新版的Linux下的hashcat进行爆破 仅此版本支持该模式
提示说八位数字,就生成了一个纯8位数字的字典(word.list)用使用高算力设备进行爆破三组数字,过程持续两小时有余:
part1:hashcat64.exe -m 13100 $krb5tgs$23$*De1CTF2020$test.local$part1/De1CTF2020*$b9bac2cd9555738bc4f8a38b7aa3b01d$12befde687b62d10d325ebc03e0dd0d6bca1f526240dfa6d23dc5bcafc224591dcf4ba97bf6219cfbe16f1b59d289800fdcc8f051626b7fe0c2343d860087c45b68d329fd1107cebe4e537f77f9eea0834ae8018a4fe8518f1c69be95667fd69dcc590d3d443a8530ff8e38ee7f7b6e378d64a8b43b985bcc20f941947ea9e8463fd7e0fa77f284368b9b489f6d557da1e02990cfc725723e5d452ff6e659717947805b852ad734c5acc8011e535b96cef3af796610196d31c725362f7426e0cf92985ffe0717baaf5066fdba760b90e2c9b7e15bc9a4952cff47d4a092d3be6128997f9ff85dbafb85a5569b5d021b2a23c6371cbdf8beaa68b332e6ba1c1a8dc43c50695498ed8c2dfbf11760af35e1b913cd36b8015df37a146d2696c8b6b5f2ce375f2674acc0ce04aa98b9d21291466ce7a2aeb5a72fda17fa53e5b41df67d3898457d05fc899096092b3aa5bc333cb75eb5eee4b1c33356e72d9d28d6d674a5e47f64c72afb580e8d4f713a5ae265a4c825c39c19313a532a23c27eaf24bcde29c5e65c13cc057e0db72094bcedb6049574e35e511847f460180ddd78f4c9187345b1068bd608ca238c20d200ffa7e3891d076fe6fcef93d044c79f5ec9fb33561a35acf785b2a203df6d07e39161d9d3cedbe6d4394bd2bf43e545acd03f796c7863d684f9db4a5eef070f71e58a4882c2387d0705f4bed32fd7986dd672a15f6cfa56fe127af7c157216b2ea4f61ab7963d9dcaf4bb9222a7cba86d6a5e6c24833ffbf1957d90224764a01e0cb5a90f12dfea4ddaef23e30c2bdafcbcd99031db5d0698c1a050fc679213a8b81b854c08686f43241a4ec937c71cd09c9519fa2bba3aa845c4e84dbd6d9bbc3a62c876fb4c30bfa7960f0f51587ece14a31add698b1b9743e14fc343394f8a346c8e24cc8c26a8f8246f6a68928d0118dea81fea9976af3c57fa4c764f565e458e065d5a2a3dd1b083f7851d4ae1b791ada853e9a20e5b169ea0b8b582711f04df4dad8b461771dda5fca11c3f8f82d85e657bbd57d12cf15c8bbce7ad6cd1ebf540c45aefd4aef2ec828b06f208bd57be6a5529481b9f8b8fad5962e86b349a720ec2a1380ed711ee0261b29383907dae6f7a45d3fff54efae7ace1f4d7193f4a4d932699a41c3deb3ba9934278942e8f09ecd4339de4059dd3ff06b78e773b6ab9826df7ea2a443dddd55cdf79db1f76e2f05105e6cc5f0c4bd494b9556d921c6cb3fa48d1ddd27cf077ebd3e44b716fc74d1115b293e348fb9676e6727a3a97a7c2b86e8b83d8f90b9bf628c71e56aabcac381a32d493db3f255378c498a0bf527a9677cb81ec89911a9b09d6ffe16e2f2de63728439f8275d9f6feac2da860c5aab772034b2b0b962c033f8102ac86b2a9b07a82e9c70be65fe371e9d296afbe0e7272b90256428553c6a4fb0a8f5290098e4dad4021d99a65f2a3fa4ad0d2f ?d?d?d?d?d?d?d?d -a 3 --force
part2:hashcat64.exe -m 18200 $krb5asrep$23$De1CTF2020@test.local:2a00ca98642914e2cebb2718e79cbfb6$9026dd00f0b130fd4c4fd71a80817ddd5aec619a9b2e9b53ae2309bde0a9796ebcfa90558e8aaa6f39350b8f6de3a815a7b62ec0c154fe5e2802070146068dc9db1dc981fb355c94ead296cdaefc9c786ce589b43b25fb5b7ddad819db2edecd573342eaa029441ddfdb26765ce01ff719917ba3d0e7ce71a0fae38f91d17cf26d139b377ea2eb5114a2d36a5f27983e8c4cb599d9a4a5ae31a24db701d0734c79b1d323fcf0fe574e8dcca5347a6fb98b7fc2e63ccb125a48a44d4158de940b4fd0c74c7436198380c03170835d4934965ef6a25299e3f1af107c2154f40598db8600c855b2b183 ?d?d?d?d?d?d?d?d -a 3 --force
part3(NTLM v2 hash):hashcat64.exe -m 5600 De1CTF2020::TEST:56886f90fcb73ded:b5991cc2a0d585d0f813358eaafc7412:0101000000000000130cb9102308d601d2290bc0c25617a80000000002000800540045005300540001000c0044004d0032003000310032000400140074006500730074002e006c006f00630061006c000300220064006d0032003000310032002e0074006500730074002e006c006f00630061006c000500140074006500730074002e006c006f00630061006c0007000800130cb9102308d60106000400020000000800300030000000000000000000000000100000ecaa3d44ddc464026c453206813aafa0b918f2ad43d497ef8fb6beb2083258a40a0010000000000000000000000000000000000009001e0048005400540050002f0074006500730074002e006c006f00630061006c000000000000000000 ?d?d?d?d?d?d?d?d -a 3 --force
hashcat -m 19700 -a 3 ./part_x_hash.txt ./word.list --force

life
题目描述:No Game No Life!
链接:https://pan.baidu.com/s/1x2zeTxYKOsbEy31J9ANv6Q
提取码:g3l6
下载附件得到一张图,图名为game,内容是动漫游戏人生剧场版宣传报,binwalk -e 分离得到一张图片和一个加密的压缩包,推测压缩包加密的txt里面是flag
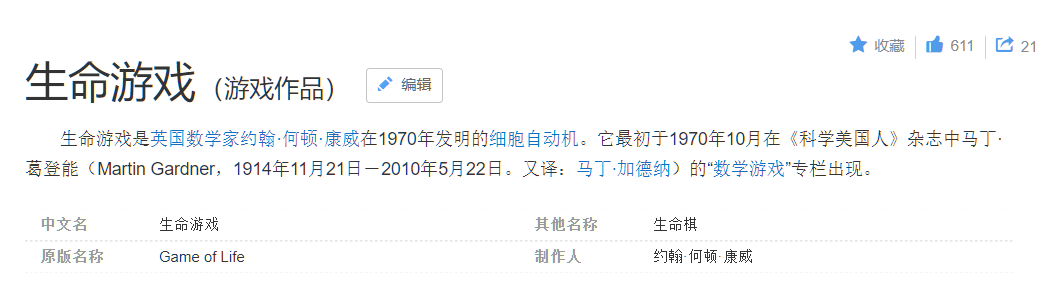
然后这张图片,刚开始以为是二维码缺失定位脚,然后在还原的时候队友发现像素点是27*27的格式,同时缺少存放格式化信息的数据块,根本无法还原二维码。然后推测可能是DataMatrix,但是找了多个识别工具都无果,转而改变方向。重新思考本题,题目叫life,给的描述是No Game No Life!,附件名为game.jpg,然后搜索game of life,查到一个life game即生命游戏
然后找到一个在线游戏网站,把图片内容构造出来,按照图片上的像素点位置点出图案,然后进行一次单步操作,可得一个二维码:
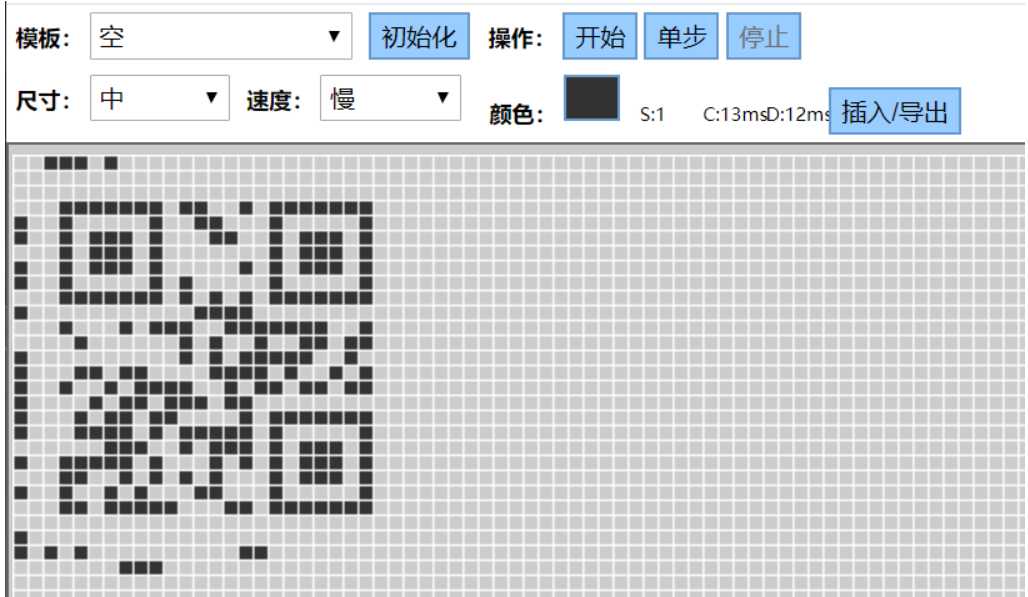
扫码即可得到解压密码:AJTC8ADEVRA13AR
解压zip包,得到一个txt文件,观察文件名txt.pilf.txt,而中间的pilf正是flip的翻转,其词义也是翻转,于是联想到将文件内容进行翻转,先翻转内容解base64,然后发现有D7,D7倒一下就是7D,于是就再将结果翻转decode('hex'),即可得到flag
a='0QjN1MTM0MTN0QjN3ImNjNzM3QTNmdTN3MTNmdzMzcjNxcjM3QTNmdDN2gzMzUjZ2czM0YDZzMjMxcDZ'
a=a[::-1].decode('base64')
flag=a[::-1].decode('hex')
print flagmc_easybgm
打开网页查看源码发现提示,根据提供的路径找到MP3文件并下载到本地:
链接:https://pan.baidu.com/s/1bRXt7AYh2I_XjIOsOjsLiA
提取码:wjc4
使用AU打开音频分析无果,然后队里师傅听歌识曲判断出了歌名,然后碰巧MP3stego用歌名作为密钥(moogcity2)可以解出一个txt,然后题目给了一个hint:easy stego,所以刚开始一直走错了方向,后来学到了mp3音频帧存在帧头信息,具体分析可见下方链接:
https://blog.csdn.net/jeffchenbiao/article/details/7332863?%3E
https://www.eefocus.com/lynn19861207/blog/10-03/187260_eae32.html
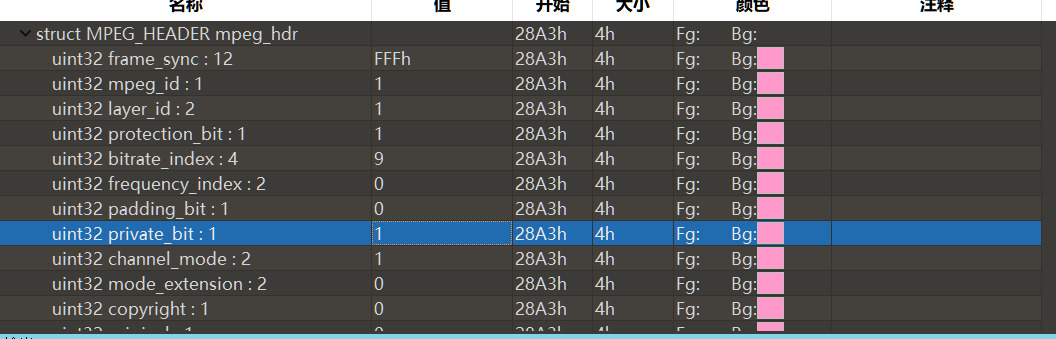
发现保留字位即private_bit位可控写入信息,猜测存在隐写
然后这题是以往出过的考点,详情可见:https://www.cnpanda.net/ctf/342.html
修改脚本为:
import re
import binascii
n = 10405
result = ''
fina = ''
file = open('C:/Users/lenovo/Desktop/bgm.mp3','rb')
while n < 1369844 :
file.seek(n,0)
n += 417
file_read_result = file.read(1)
read_content = bin(ord(file_read_result))[-1]
result = result + read_content
print result输出:
101111101000010010101110011010101000001001010110110011000010001011111010001000101000110001001110000011001110101011111010001011100110001000101100010010101100001011001100111011001001011010110010111110100000110000101110111110101100110010110110000011001100011010001100110011001110101011011110011000100010101011000010100011001010011000100010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000然后后面那一大堆00串我们都是不要的,我们给他保留到8的倍数刚好完成后,后面的0全部舍弃,同时将保留的数据反转,并且8个一组分割开,转成字符串即可
payload:
result = '010001000110010100110001010000110101010001000110011110110101011100110011001100010110001100110000011011010011001101011111011101000011000001011111010011010110100100110111001100110100001101010010001101000100011001110100010111110101011100110000011100100011000101000100010111110100010000110011011010100100000101010110011101010010000101111101'
textArr = re.findall('.{'+str(8)+'}', result)
# textArr.append(result[(len(textArr)*8):])
for i in textArr:
fina = fina + chr(int(i,2)).strip('\n')
print fina最后输出