咕咕咕好久的博客更新啦~这里来更新一下之前就写好但是一直没放的西湖论剑2020 MISC WriteUp
yusa_yyds
链接:https://pan.baidu.com/s/1h0Yp-osbshtIX0gNRoVsWQ
提取码:0hef
下载附件得到game.pcapng,查看流量包发现是一堆usbdata
观察有发送数据的字段(Leftover Capture Data字段),即IP==2.15.2与HOST之间通信的报文:
分析该USB流量分析为键盘或者手柄
然后通过usb的接入流量数据判断设备为Xbox360手柄
那么开始分析下面的2.15.2的数据。观察多个报文的时间间隔:
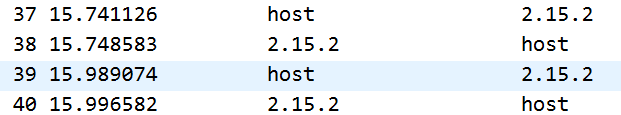
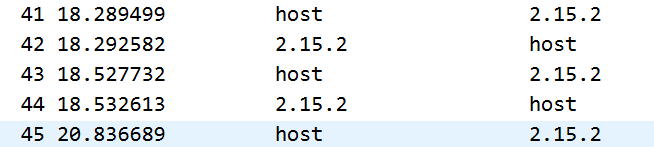
有一些报文时间间隔明显大于其他的时间间隔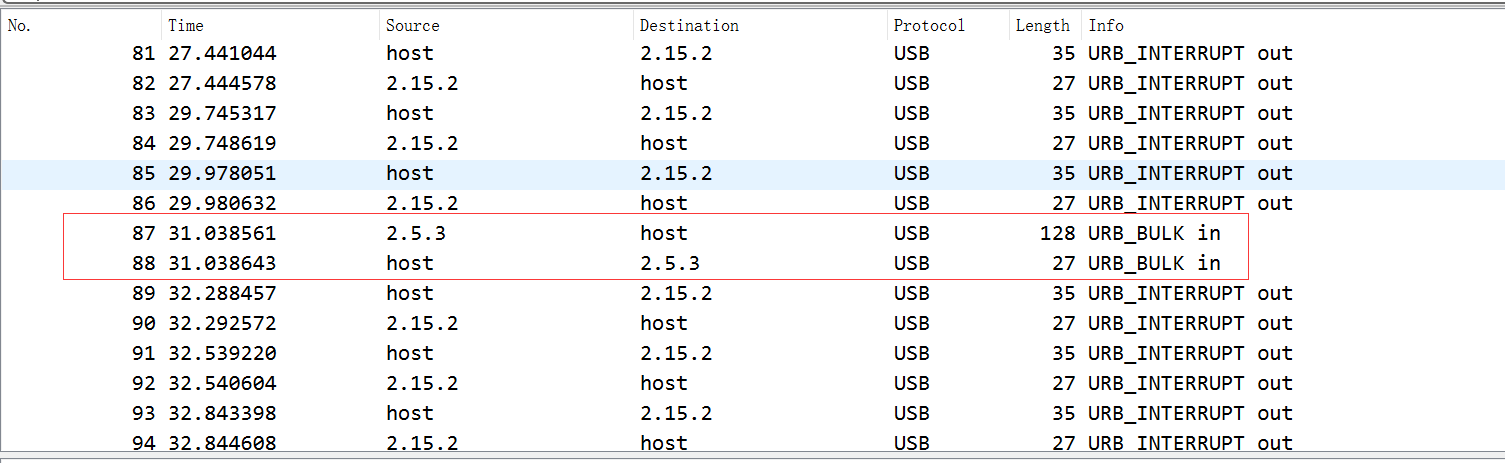
观察除去红框中URB_BULK in的其他数据包,发现以一个大时间间隔以及中间的四个包为一组,赛后根据官方wp可以知道:通过时间可以发现,中间有明显的断电。且xbox的流量在测试过程中可知,震动一次会有4个包出现)
那么通过肉眼分辨即可。能得到分别震动 1 1 4 5 1 4次
最后取md5
得到c4d038b4bed09fdb1471ef51ec3a32cd
Yusapapa
打开网站,首先看到了Yusa(女神),然后F12打开,发现一串密文
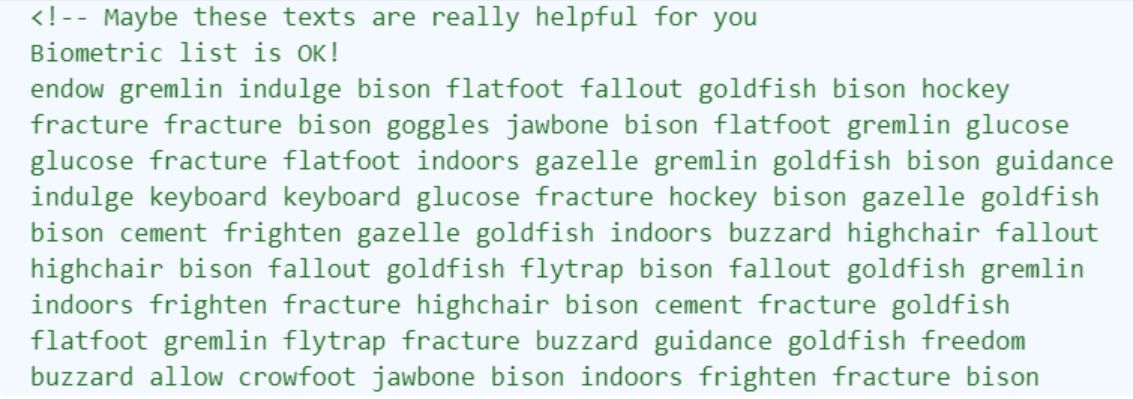 直接搜了一下,发现有个PGP词汇表,然后在记事本里一个个替换后是一串十六进制,解得
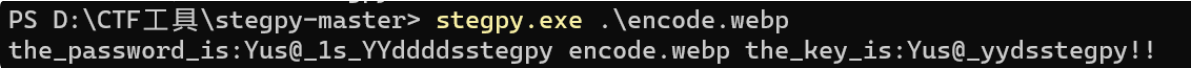
直接搜了一下,发现有个PGP词汇表,然后在记事本里一个个替换后是一串十六进制,解得  然后下载得到hint.rar 和encode.png , 然后网页上还存在一张有关"Yusa"的照片(encode.webp),然后下载这个webp文件,利用stegpy工具(用法参照此篇博客),解得压缩包密码:
然后下载得到hint.rar 和encode.png , 然后网页上还存在一张有关"Yusa"的照片(encode.webp),然后下载这个webp文件,利用stegpy工具(用法参照此篇博客),解得压缩包密码:
 然后等官方放了hint,找到一个叫invisible secret的工具,用Unhide Files选项,选择hint.jpg,选择Blowfish加密,密钥为Yusa,找到了隐藏文件:
然后等官方放了hint,找到一个叫invisible secret的工具,用Unhide Files选项,选择hint.jpg,选择Blowfish加密,密钥为Yusa,找到了隐藏文件:
 然后看了一下脚本,写了个解密脚本:
然后看了一下脚本,写了个解密脚本:
import os,random
from PIL import Image,ImageDraw
hide=Image.open('encode.png').convert('RGB')
a,b = hide.size
R = []
G = []
B = []
for x in range(a):
for y in range(b):
R.append(bin(hide.getpixel((x,y))[0]).replace('0b','')[-1])
G.append(bin(hide.getpixel((x,y))[1]).replace('0b','')[-1])
B.append(bin(hide.getpixel((x,y))[2]).replace('0b','')[-1])
flag = []
for i in range(len(R)):
flag.append(int(R[i])^int(G[i])^int(B[i]))
img=Image.new('RGB',(a,b),(255,255,255))
for x in range(a):
for y in range(b):
if flag[x*b+y] == 0:
img.putpixel((x,y),(0,0,0))
else:
img.putpixel((x,y),(255,255,255))
img.save('flag.png')最后得到flag.png:

Barbar
链接:https://pan.baidu.com/s/1pZUqv_aBi8pEai-3W2Sp6A
提取码:3uza
首先拿到这张图片,binwalk以后发现有zip,foremost提取以后打开压缩包,发现提示密码为32字节,无法爆破: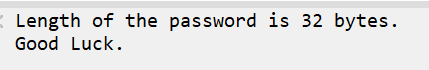
然后扫码可得一串信息,这里这串信息是零宽度字符隐写:
关于零宽度字符隐写的详细文章,可参照本篇文章
然后零宽度字符隐写,利用不同的在线网站,识别的结果可能是不一样的,这里对常见的几个网站进行一个整理:
- https://330k.github.io/misc_tools/unicode_steganography.html
- https://offdev.net/demos/zwsp-steg-js
- https://yuanfux.github.io/zero-width-web/
- https://www.mzy0.com/ctftools/zerowidth1/
github项目的话为:
然后我们可以发现,二维码识别的结果在第三个网站可以解密出信息,那么这个就是压缩包的密码:
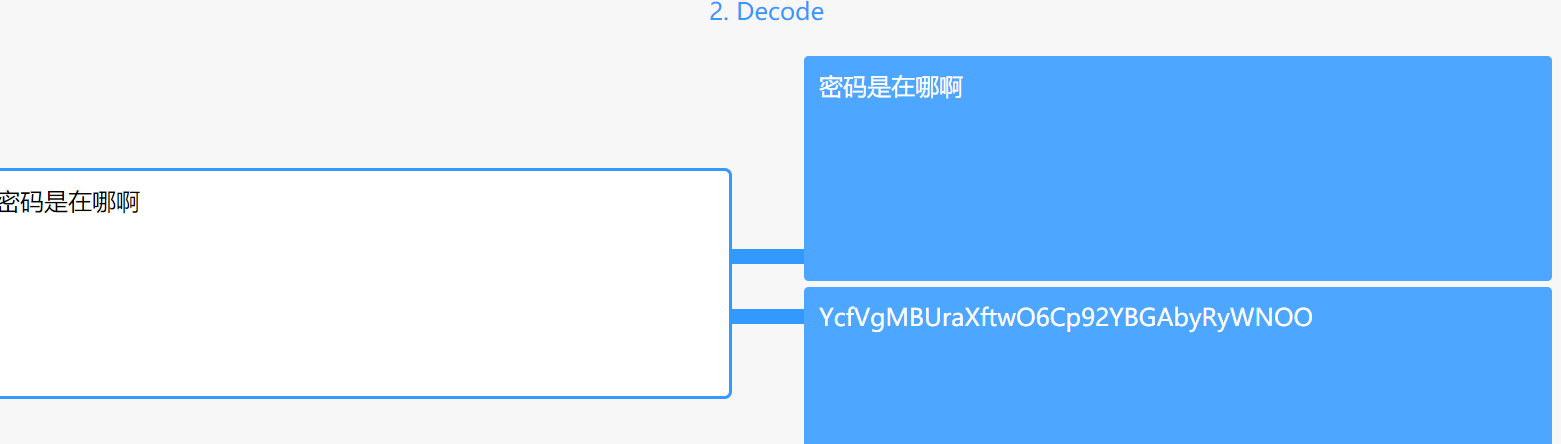
然后得到一个看起来坏了的qrcode和一个word文档,先看word文档,里面没有什么隐写的地方,所以想到修改后缀为.zip,依次查看里面的文件,在document.xml这个文件里可以发现一大串base64,复制的时候把所有的
都要删掉:
iVBORw0KGgoAAAANSUhEUgAAAGwAAABsCAYAAACPZlfNAAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAAAJcEhZcwAAEnQAABJ0Ad5mH3gAAAckSURBVHhe7ZHRauw6EATv///0uX4QRi7NqtIZe5OQFBQL6u5xIP8d/NtpVJtZ8ttzw/bH27VAjWozS357btj+eLsWqFFtZslvzw3bH2/XAjWqzSz57blh++PtWjCNtG9079meOSWWE+szp+R4q4uvNNK+0b1ne+aUWE6sz5yS460uvtJI+0b3nu2ZU2I5sT5zSo63uvhKI+0b3Xu2Z06J5cT6zCk53rSwzQ3uKbGcsJ9Kqs6sYX3mJjnetLDNDe4psZywn0qqzqxhfeYmOd60sM0N7imxnLCfSqrOrGF95iY53rSwzQ3uKbGcsJ9Kqs6sYX3mJvG/ANjBFLuX5iZJ81RSdWYNb4D0A4bdS3OTpHkqqTqzhjdA+gHD7qW5SdI8lVSdWcMbIP2AYffS3CRpnkqqzqyhDTtoObE+c0qqzuzdVN+YJVVnllSdi6P3Eg6I5cT6zCmpOrN3U31jllSdWVJ1Lo7eSzgglhPrM6ek6szeTfWNWVJ1ZknVuTh6L+GAWE6sz5ySqjN7N9U3ZknVmSVV5+LofRgeuBvep6Tq7Ezp7gnvUSP+C9IPpPA+JVVnZ0p3T3iPGvFfkH4ghfcpqTo7U7p7wnvUiP+C9AMpvE9J1dmZ0t0T3qOGNtKDXex7zFNJNyfWZ07J0hnvL+Hgaex7zFNJNyfWZ07J0hnvL+Hgaex7zFNJNyfWZ07J0hnvL+Hgaex7zFNJNyfWZ07J0hnvJyykcH+3JM2pYX3LSdony6J9EPu7JWlODetbTtI+WRbtg9jfLUlzaljfcpL2ybJoH8T+bkmaU8P6lpO0T+IFP0hTqhsdieXG3XuTLJ3x/mGWAzClutGRWG7cvTfJ0hnvH2Y5AFOqGx2J5cbde5MsnfH+YZYDMKW60ZFYbty9N8nSGe8nLJA0//OqYf2/f9ibNaz/9w97s4b1//5hb9aw/vF2LZik6symdPdd7PvMTeMT/evAJFVnNqW772LfZ24an+hfByapOrMp3X0X+z5z0/hE/zowSdWZTenuu9j3mZtG3B+/J/EB9GmK7Zl3JVVn1rB+Ox+/JzYg7NMU2zPvSqrOrGH9dj5+T2xA2KcptmfelVSdWcP67Xz8ntiAsE9TbM+8K6k6s4b1b8j3BcK+mWJ7yw3bM6fvpvgbrg8G+2aK7S03bM+cvpvib7g+GOybKba33LA9c/puir/h+mCwb6bY3nLD9szpu1n+hvF+wgKxnNzd/245Nayv+fg90YHk5O7+d8upYX3Nx++JDiQnd/e/W04N62s+fk90IDm5u//dcmpYX/Px+xI7kGL3urlhe+aUVJ2dxHKijfSgYfe6uWF75pRUnZ3EcqKN9KBh97q5YXvmlFSdncRyoo30oGH3urlhe+aUVJ2dxHKyNNIDBu+lkqrTkVjexe5rPn5PbJDCe6mk6nQklnex+5qP3xMbpPBeKqk6HYnlXey+5uP3xAYpvJdKqk5HYnkXu/+BXAvbnLDf9d3Y9y03bM+88PpALCfsd3039n3LDdszL7w+EMsJ+13fjX3fcsP2zAuvD8Rywn7Xd2Pft9ywPfPC64PBPiWWE/Z/mk9zfCP7IPuUWE7Y/2k+zfGN7IPsU2I5Yf+n+TTHN7IPsk+J5YT9n+bTLF+o/ohZYjnp9rsSy1PsHnOTLC/VaJZYTrr9rsTyFLvH3CTLSzWaJZaTbr8rsTzF7jE3yfJSjWaJ5aTb70osT7F7zE2yvNggJb3HPjWsz5waT/eN5cLtHwjvsU8N6zOnxtN9Y7lw+wfCe+xTw/rMqfF031gu3P6B8B771LA+c2o83TeOG9lB9mlKdWOnYf00f1pSdeD1wWCfplQ3dhrWT/OnJVUHXh8M9mlKdWOnYf00f1pSdeD1wWCfplQ3dhrWT/OnJVXn4uh9GB4g3ZywbxLLifWZd02JF/bBbk7YN4nlxPrMu6bEC/tgNyfsm8RyYn3mXVPihX2wmxP2TWI5sT7zrim6sA+kOTWqzaxRbWZTunvCe5ToF/VAmFOj2swa1WY2pbsnvEeJflEPhDk1qs2sUW1mU7p7wnuU6Bf1QJhTo9rMGtVmNqW7J7xHyfJiA4P71BTbW07YTzWsr/n4PbGBwX1qiu0tJ+ynGtbXfPye2MDgPjXF9pYT9lMN62s+fk9sYHCfmmJ7ywn7qYb1P5DvC8T6lhu27+aG7bs5sT7zw+uDYX3LDdt3c8P23ZxYn/nh9cGwvuWG7bu5YftuTqzP/PD6YFjfcsP23dywfTcn1md+eH0gzCmpOrOk6sySNKeG9ZlTo9rsJMebFraSqjNLqs4sSXNqWJ85NarNTnK8aWErqTqzpOrMkjSnhvWZU6Pa7CTHmxa2kqozS6rOLElzalifOTWqzU6yvOgAuUksN57ef3VuLAs7yNwklhtP7786N5aFHWRuEsuNp/dfnRvLwg4yN4nlxtP7r873/Pv3P5ySkc0n6rmgAAAAAElFTkSuQmCC转码得到一个aztec码: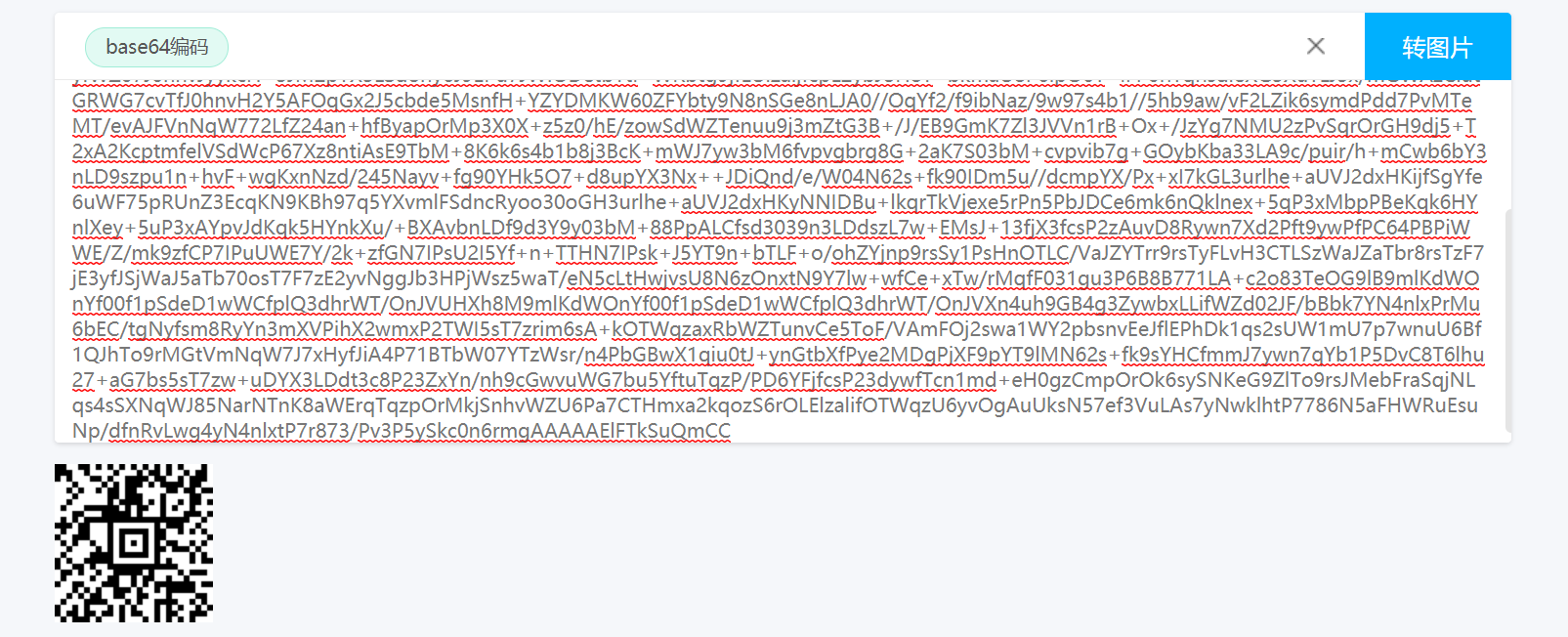
扫码得到 di`f{e1c64e14db14c6bb8faabab5bd7be1dc}: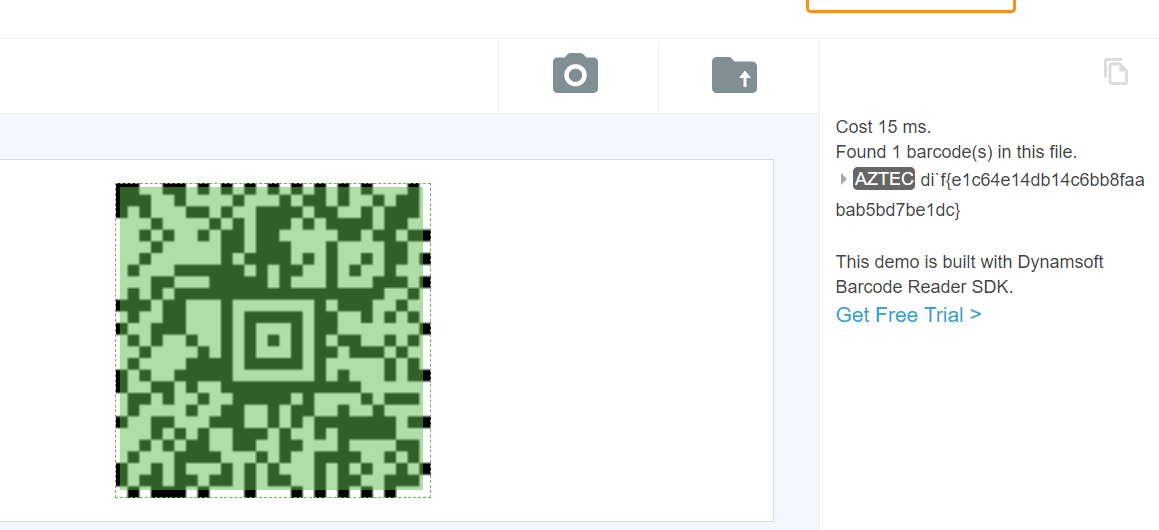
然后那个看起来是损坏的qrcode,补全定位脚扫码得到的信息没有任何作用,也没有零宽度隐写,那么这里就涉及一个新知识:
这个损坏的二维码的图案,实际上是一种基于颜色和像素的编程语言:piet
这种编程语言有在线的解释器,搜索npiet即可找到:npiet
然后上传完图片以后,选择最下面红框这个选项: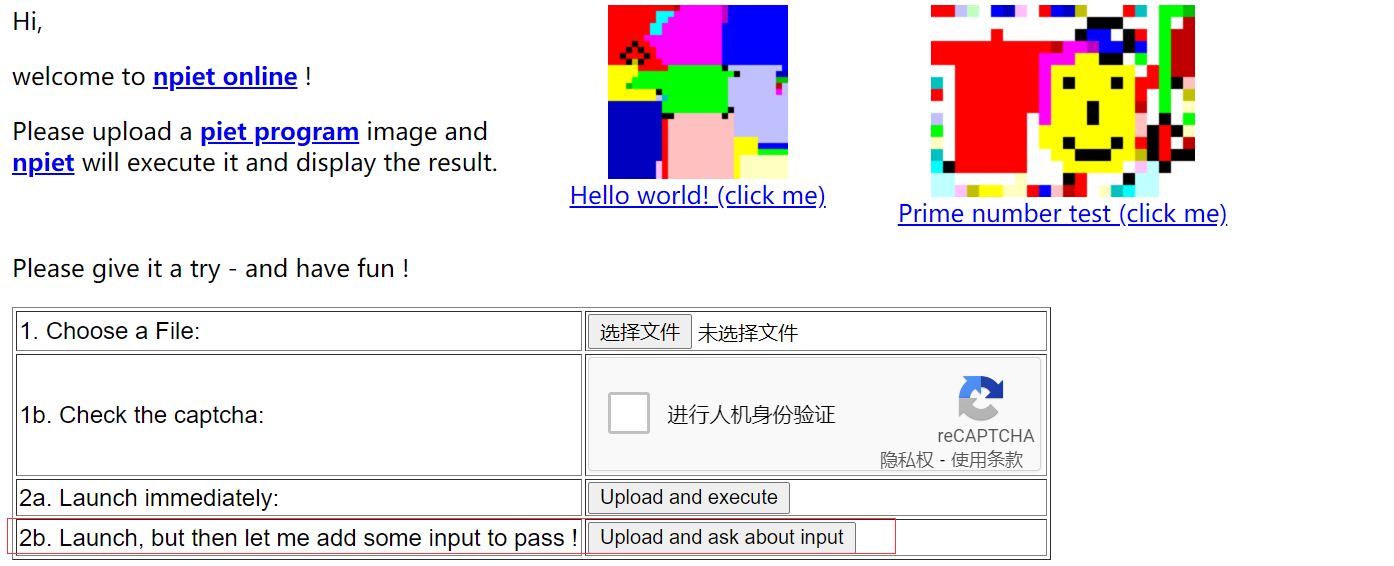
输入上面的aztec识别结果: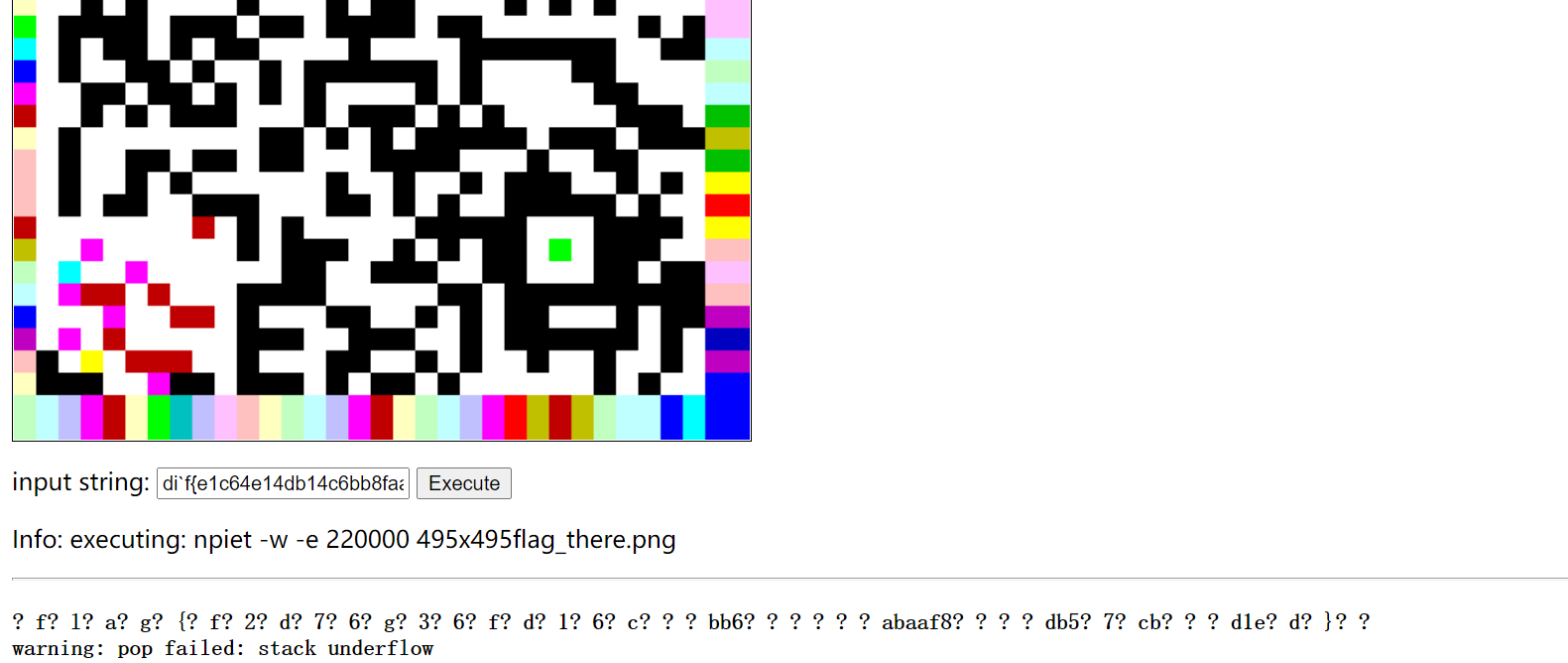
得到最后flag:flag{f2d76g36fd16cbb6abaaf8db57cbd1ed}
指鹿为马
就是生成一个像马的鹿就好了,线性组合一下,脚本如下
# Source.py here
def main():
pic_name = "deer2.png"
if check(pic_name)>=100000:
return False
ma = load_horse()
lu = load_deer()
k = 1
trainingSet = np.append(ma, lu).reshape(2, 5185)
testSet = load_test(pic_name)
neighbors = getNeighbors(trainingSet, testSet[0], k)
result = getResponse(neighbors)
return result == 0
from PIL import Image
from scipy.spatial import distance
import matplotlib.pyplot as plt
import numpy as np
import math
h = Image.open('horse.png')
d = Image.open('deer.png')
horse = np.array(h.convert('L')).reshape(-1)
deer = np.array(d.convert('L')).reshape(-1)
def test(a,b,c,d,e,f):
dat = []
for i in range(deer.size):
res = 0
if deer[i] != 0:
res += max(deer[i] // a - b, 0) * c
if horse[i] != 0:
res += max(horse[i] // d + e, 0) * f
dat.append(res)
dat = np.array(dat, np.uint8)
img = Image.fromarray(dat.reshape(72,72),"L")
img.save("deer2.png")
for i in range(100):
for j in range(i):
print(i,j)
test(1, 100, 1, i, 0, j)
if main():
print(i, j)
exit()这里提供一个比较详细的有关此题的wp:https://blog.csdn.net/qq_43615309/article/details/109049780
以及官方wp:https://mp.weixin.qq.com/s/lDAbWmblJ1QO9f7nXjEOnQ